Tailor your MacBook experience to your unique preferences with our simple setup guide, where we'll cover the basics, such as creating your Apple ID and customizing your desktop. Whether you're a tech enthusiast or a first-time Mac user, this guide will help you make the most of your new MacBook.
Blog
The complete guide to business phones in 2024

In 2024, choosing the right phone system is more important than ever to stay ahead of the competition. This comprehensive guide will walk you through the latest business phone system advancements, including Voice over Internet Protocol (VoIP), which has become the preferred choice for companies looking to enhance their communication strategies.
Optimize your Windows 11 experience by getting rid of bloatware

Want to make the most of your Windows 11 PC? Removing bloatware is a crucial step. Learn how to easily uninstall unnecessary applications and declutter your system for a smoother and more efficient experience.
What is bloatware?
Bloatware, also known as junkware or crapware, refers to preinstalled software on your device that is often unnecessary and takes up storage space and resources.
AI-powered browsers: What users can expect

Modern web browsers such as Google Chrome, Safari, and Microsoft Edge have incorporated AI (artificial intelligence) features that enhance user experience. By leveraging AI, browsers will offer smarter search results, better security, and a more personalized browsing experience, fundamentally changing how we navigate the digital world.
Stay ahead of common cyberthreats

Cybercriminals are constantly coming up with new ways to infiltrate IT systems. You've invested countless hours and resources building your business; don't let a cyberattack undo all your hard work. A great way to start fortifying your company’s defenses is to learn all about common cyberthreats and how to keep them at bay.
A guide to buying a projector for your office

Maximize the impact of your presentations with the ideal projector for your office. This article will help align projector capabilities with your business objectives, allowing you to make a smart choice when purchasing a projector.
Brightness
If your projector doesn’t produce enough brightness, it will yield muddy and blurred images, even when the lights in the room are dimmed or turned off.
Leverage these VoIP services to unlock business growth
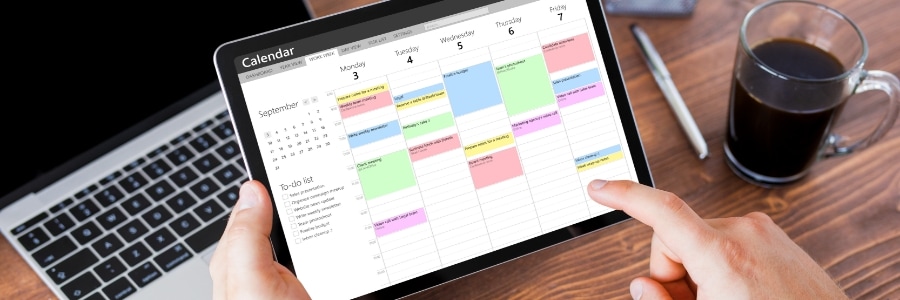
How to share your Outlook calendar like a pro
Leveraging AI to drive eCommerce business growth
Picking the MSP for you: The basics and what to consider

Small and medium-sized businesses often stretch themselves thin, with IT management becoming a significant burden. Seeking external IT support through a managed IT services provider (MSP) is a common solution. However, understanding the role of an MSP and choosing the ideal partner can be confusing without a little help.